- Infos im HLRS Wiki sind nicht rechtsverbindlich und ohne Gewähr -
- Information contained in the HLRS Wiki is not legally binding and HLRS is not responsible for any damages that might result from its use -
VPN: Difference between revisions
| Line 42: | Line 42: | ||
# ca-file = /usr/share/ca-certificates/mozilla/Deutsche_Telekom_Root_CA_2.crt | # ca-file = /usr/share/ca-certificates/mozilla/Deutsche_Telekom_Root_CA_2.crt | ||
A user certificate is '''not''' required. | Remarks: | ||
* A user certificate is '''not''' required. | |||
If your Openssl library is configured correctly and your certificate bundles are installed properly it should neither be necessary to explicitly | * If your Openssl library is configured correctly and your certificate bundles are installed properly it should neither be necessary to explicitly specify the CA certificate (cf. last line of the config file template given above). | ||
* The VPN gateway uses a DFN certificate which is issued below the root CA tree of the German Telekom, one of the CA's trusted by most browsers. | |||
The VPN gateway uses a DFN certificate which is issued below the root CA tree of the German Telekom, one of the CA's trusted by most browsers. The trusted-cert (cf. next to last line in config file template given above) is the digest of the server's certificate which is subject to change every couple of years. It might hence be wise not to specify this in your config file. | * The trusted-cert (cf. next to last line in config file template given above) is the digest of the server's certificate which is subject to change every couple of years. It might hence be wise not to specify this in your config file. | ||
Revision as of 16:39, 19 May 2020
Access HLRS compute service using VPN
Access to HLRS compute platforms requires a registration of the clients IP address in the firewall. If the IP address is not static a connection via VPN is recommended.
To use this feature, please contact your project supervisor and ask him to add the vpn-hww resource in the HLRS user database. Install the Fortigate software on your laptop. The Software can be downloaded at
https://www.forticlient.com (Windows, Mac) https://github.com/adrienverge/openfortivpn (Linux and Mac)
On Fedora, OpenSUSE, and latest Ubuntu openfortivpn is available via packet manager.
On Mac OSX openfortivpn can also be installed via Homebrew or Macports.
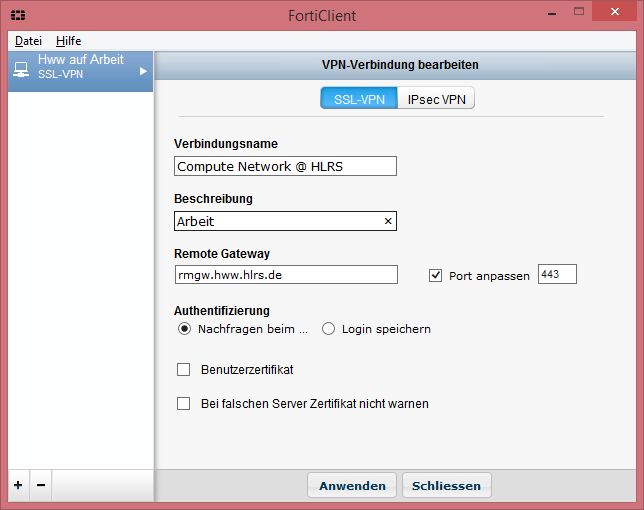
Configuration of Fortinet VPN client on Windows
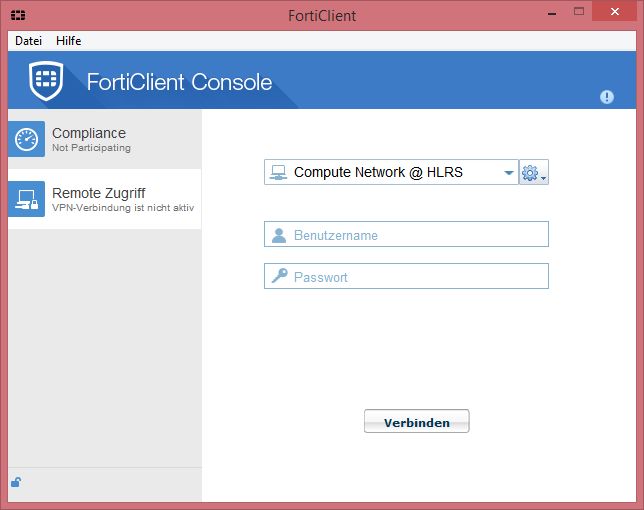
Using the VPN on Windows
Type your login and password to connect. If this works, you are able to login on the frontend servers using ssh e.g.
ssh -l <your_login> hawk.hww.hlrs.de
Configuration of openfortivpn on Linux
Please insert the following data into your config file (probably /etc/openfortivpn/config):
host = rmgw.hww.hlrs.de port = 443 username = <your username> # trusted-cert = 5338851771baa67d1a29fa8df7d49ddbd83cbbd517c78e032bf5ab305eaba3f8 # ca-file = /usr/share/ca-certificates/mozilla/Deutsche_Telekom_Root_CA_2.crt
Remarks:
- A user certificate is not required.
- If your Openssl library is configured correctly and your certificate bundles are installed properly it should neither be necessary to explicitly specify the CA certificate (cf. last line of the config file template given above).
- The VPN gateway uses a DFN certificate which is issued below the root CA tree of the German Telekom, one of the CA's trusted by most browsers.
- The trusted-cert (cf. next to last line in config file template given above) is the digest of the server's certificate which is subject to change every couple of years. It might hence be wise not to specify this in your config file.