- Infos im HLRS Wiki sind nicht rechtsverbindlich und ohne Gewähr -
- Information contained in the HLRS Wiki is not legally binding and HLRS is not responsible for any damages that might result from its use -
Secure Shell ssh: Difference between revisions
No edit summary |
|||
| Line 24: | Line 24: | ||
=== if you can't get a connection === | === if you can't get a connection === | ||
this may have 3 causes: | this may have 3 causes: | ||
# Your workstation is not known by the firewall. Please contact Your HLRS contact person (adviser/Betreuer), or submit a bug-report to accounting via the [http://www.hlrs.de/organization | # Your workstation is not known by the firewall. Please contact Your HLRS contact person (adviser/Betreuer), or submit a bug-report to accounting via the [http://www.hlrs.de/organization/trouble-ticket-submission-form/ Trouble Ticket Submission Form] providing Your username and the static IP Address You want to access from. | ||
# The HWW platform, you're trying to connect to, is currently not running. Please check the appropriate [http://www.hlrs.de/systems/platforms/status/ status] page for your platform. | # The HWW platform, you're trying to connect to, is currently not running. Please check the appropriate [http://www.hlrs.de/systems/platforms/status/ status] page for your platform. | ||
# Your ssh client is setuid root. Please remove setuid root bit or use -P (for ssh) resp. -L option (for scp). | # Your ssh client is setuid root. Please remove setuid root bit or use -P (for ssh) resp. -L option (for scp). | ||
Revision as of 10:28, 22 February 2016
Installation
Secure shell is the exclusive way to get into the secure environment of the HWW machines. Commands like telnet, ftp as well as the r-cmds are NOT allowed and therefore are rejected by the firewall.
On HWW platforms the ssh software is installed. The user is responsible for installation of ssh on his platform.
The source of OpenSSH is available from
- HOME page of OpenSSH Alternatives for other platforms like MS Windows can also be found on this site.
For details on the licensing see the external link HOME page of OpenSSH
For details on the licensing see the copyright notice. Please read first the files README and INSTALL.
Please be aware to run the latest version of ssh client software. Most operating systems provide insallable packages and update mechanism.
Tips and hints
if you can't get a connection
this may have 3 causes:
- Your workstation is not known by the firewall. Please contact Your HLRS contact person (adviser/Betreuer), or submit a bug-report to accounting via the Trouble Ticket Submission Form providing Your username and the static IP Address You want to access from.
- The HWW platform, you're trying to connect to, is currently not running. Please check the appropriate status page for your platform.
- Your ssh client is setuid root. Please remove setuid root bit or use -P (for ssh) resp. -L option (for scp).
If you encounter any problems while connecting with ssh, please use -v option to get more detailed messages from ssh.
Filetransfer without password (scp) using Protocol version 2
Login via ssh resp. Filetransfer via scp is also possible without having to enter a password. Authentification is done via a public/private key pair. The following steps have to be accomplished:
(system1 is the machine from which you logon to the target system system2)
System1 > ssh-keygen -d
Generating public/private dsa key pair.
Enter file in which to save the key ($HOME/.ssh/id_dsa): <RETURN>
Enter passphrase (empty for no passphrase): <RETURN>
Enter same passphrase again: <RETURN>
Your identification has been saved in $HOME/.ssh/id_dsa.
Your public key has been saved in $HOME/.ssh/id_dsa.pub.
The key fingerprint is:
2f:5c:18:e7:g0:3b:fb:52:g3:22:1d:3d:a4:cf:b1:57 $LOGNAME@$HOSTNAME
System1 > cd $HOME/.ssh
System1 > scp id_dsa.pub System2:sys1.pub
System1 > chmod 700 $HOME/.ssh
System2 > cd $HOME/.ssh
System2 > cat $HOME/sys1.pub >> authorized_keys2
System2 > chmod 700 $HOME/.ssh
The key generation with ssh-keygen has only to be done once. The public key in the file $HOME/.ssh/identity.pub can be used for as many systems as needed.
Further information regarding ssh can be found at external link http://www.cs.hut.fi/ssh/ or at external link DATA FELLOWS - F-Secure SSH A good alternative for Windows platforms is external link putty
ssh-x509 Certificate based ssh access
This access method is currently implemented for testing and evaluation purposes. Following Systems provide this service:
- yari.hww.de (NEC SX-9)
- clr3fr1.hww.de (nehalem cluster)
- frbw.dgrid.hlrs.de (BW-Grid cluster)
Be aware you need a special version of ssh-client with x509 support. Detailed information on how to set up X.509 enabled ssh can be found on our webserver at X.509-SSH.
ssh tunnel
Due to security policies inside the HWW network (all HWW platforms), general internet access is not possible. For example to get access to software repositories (svn servers), a ssh tunnel could be useful.
W A R N I N G :
If you create an ssh tunnel, any user on this system is able to access this port. Please be aware of sensitive data on your local network. E.g. if you create an ssh tunnel to your local private software repository, any users on the remote server has access to this port and is able to use this repository!
Please find the following example to get access to a svn repository.
For Linux, Mac and Unix users:
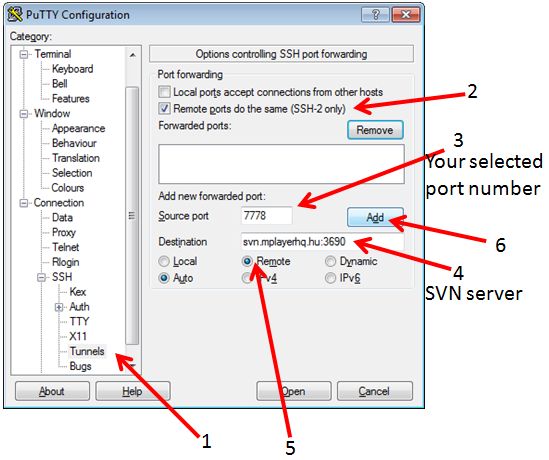
Assume the svn repository is: svn.mplayerhq.hu listening on port 3690 (default svn port) and your username on the HWW platform hermit1.hww.de is hpchugo. Then on your local workstation login and create the tunnel using following commands:
ssh -R7777:svn.mplayerhq.hu:3690 hpchugo@hermit1.hww.de
You will be asked for your password on hermit1 and get a login session. The local port on hermit1 into the created tunnel in this example is 7777. Please select a different number in the range of 5000-20000. This number must be unique for each user and each tunnel. Be aware on some platform of HWW (e.g. the cray system hermit1) round robin name service will cause multiple sessions on different login servers. The created tunnel is only available on the login server created by the ssh command above.
To use this tunnel you have to access the selected port (7777) on localhost of hermit1.hww.de:
svn co svn://localhost:7777/ffmpeg/trunk ffmpeg
on windows using putty you have to open following dialogue:
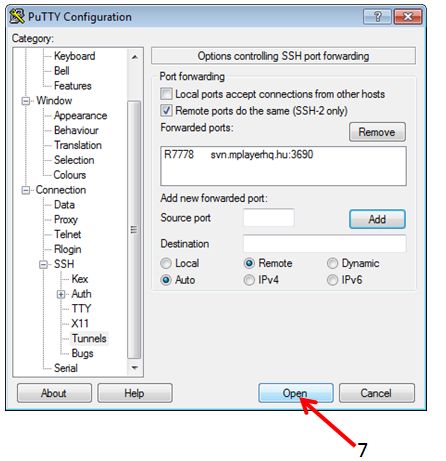
by klick on the ADD button, the dialogue should look like:
To use this tunnel you have to access the selected port (7778) on localhost of hermit1.hww.de:
svn co svn://localhost:7778/ffmpeg/trunk ffmpeg
For more information please check:
man ssh
External links (Wikipedia & Co.): ssh-tunnel german ssh-tunnel wiki german ssh-tunnel wiki english
as a second example following commands are neccessary to transfer an external WEB page into the current working dirtory on the hermit1 system:
## login and create the tunnel ssh -R7890:ftp.scientificlinux.org:80 hpchugo@hermit1.hww.de ## fetch one file from this server wget http://localhost:7890/linux/scientific/6x/x86_64/iso/readme
for tunnelling svn+ssh connections:
If you use the svn+ssh protocol to check out files you have to use a bit more workarounds since you are already using ssh to do the tunneling.
A possible solution is to start a tunnel from your laptop to the frontend through the firewall and access the repository through this tunnel. Log in to the cluster and see if the port is free
ssh cl3fr1.hww.de "netstat -l | grep 10022"
If it is in use, just pick another one for the following steps.
Make a tunnel from your laptop to the repository:
ssh -R10022:your.svnserver.com:22 -N -t -x cl3fr1.hww.de
Test the tunnel (this makes sure it works and that an entry of localhost:10022 will be added to your ssh known_hosts file such that ssh-agent works like a charm) by doing the following on the cluster:
ssh -p 10022 username@localhost
(Note that the username is the username at the other end of the tunnel!)
Add a custom protocol to your .subversion/config file on the cluster. Under the heading [tunnels] add
tunnel_ssh = $TUNNEL_SSH ssh -p 10022
Maybe you have to transfer ssh-keys in order to be able to log in password-free. Be aware that there are other users on the same host who can use this tunnel as well, so be careful how much you open. Maybe it is a better idea to temporarily genearate a separate ssh-keypair which you throw away after you are done with the svn stuff.
Finally, you can test the connection, or simply check out your sources:
svn co svn+tunnel_ssh://localhost/repos/...